Latest posts
-

Build Tesseract 5 in Conda Environment
Here’s a short guide to building Tesseract 5 from source (master branch on GitHub). I’m writing this mainly because conda offers as packages only versions of Tesseract up to 4.1.1 – at least at this moment. The other reason is...
-

PyTorch CRNN: Seq2Seq Digits Recognition w/ CTC
This article discusses handwritten character recognition (OCR) in images using sequence-to-sequence (seq2seq) mapping performed by a Convolutional Recurrent Neural Network (CRNN) trained with Connectionist Temporal Classification (CTC) loss. The aforementioned approach is employed in multiple modern OCR engines for handwritten...
-
Improving Tesseract 4's OCR Accuracy through Image Preprocessing
In this work I took a look at Tesseract 4’s performance at recognizing characters from a challenging dataset and proposed a minimalistic convolution-based approach for input image preprocessing that can boost the character-level accuracy from 13.4% to 61.6% (+359% relative...
-
PyTorch Iterative FGVM: Targeted Adversarial Samples for Traffic-Sign Recognition
Inspired by the progress of driverless cars and by the fact that this subject is not thoroughly discussed I decided to give it a shot at creating smooth targeted adversarial samples that are interpreted as legit traffic signs with a...
-

RSA: Encrypt in .NET & Decrypt in Python
So… one of my current projects required the following actions: asymmetrically encrypt a string in .NET using a public key and decrypt it in a python script using a private key. The problem that I’ve encountered was that, apparently, I...
-

Avoid a Mistake: Correctly Calculate Multiclass Accuracy
Today I held a short laboratory which tackled different metrics used in evaluating classifiers. One of the tasks required that, given the performances of 2 classifiers as confusion matrices, the students will calculate the accuracy of the 2 models. One...
-

C# Predict the Random Number Generator of .NET
This post targets to underline the predictability of the random… or better said pseudo-random number generator (PRNG) exposed by the .NET framework (aka the Random() class), under certain assumptions. Because of the nature of the implementation, 100% accuracy can be...
-

Evaluating the Robustness of OCR Systems
In this article, I’m going to discuss about my Bachelor’s degree final project, which is about evaluating the robustness of OCR systems (such as Tesseract or Google’s Cloud Vision) when adversarial samples are presented as inputs. It’s somewhere in-between fuzzing...
-

Hot Patching C/C++ Functions with Intel Pin
5 years ago, I said in one of my articles that I shall return, one day, with a method of hot patching functions inside live processes; So… I guess this is that day. What we’ll try to achieve here is...
-
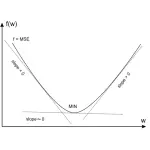
Gradient Descent Simply Explained (with Example)
So… I’ll try to explain here the concept of gradient descent as simple as possible in order to provide some insight of what’s happening from a mathematical perspective and why the formula works. I’ll try to keep it short and...
-

Bypassing ASLR and DEP - Getting Shells with pwntools
Today, I’d like to take some time and to present a short trick to bypass both ASLR (Address Space Layout Randomization) and DEP (Data Execution Prevention) in order to obtain a shell in a buffer-overflow vulnerable binary. I’ve seen this...
-

C# Making a Neural Network that plays Flappy Bird
All right, people; now that I’m done with the projects & finals for…a couple of days…I thought it would be a good idea to keep an old promise and finally publish this article too. It’s about how to make a...